Retail
The status quo in converged Enterprise information technology (IT) and operational technology (OT) networks is physical connectivity with network level segmentation, network-based intrusion detection/prevention (IDS/IDP) predicated on insecure plaintext over-the-wire communications, or a bump-in-the-wire broker-based blockchain fabric overlay. Achieving logical trusted connectivity to implement a cost-effective and highly efficient zero-trust architecture over existing network infrastructures and in-field devices requires a paradigm shift from “cyber threats” to “cyber risks” and from “multi-layer peripheral defense” to “operational resilience at the core” for long-term desirable outcomes with application security by design.
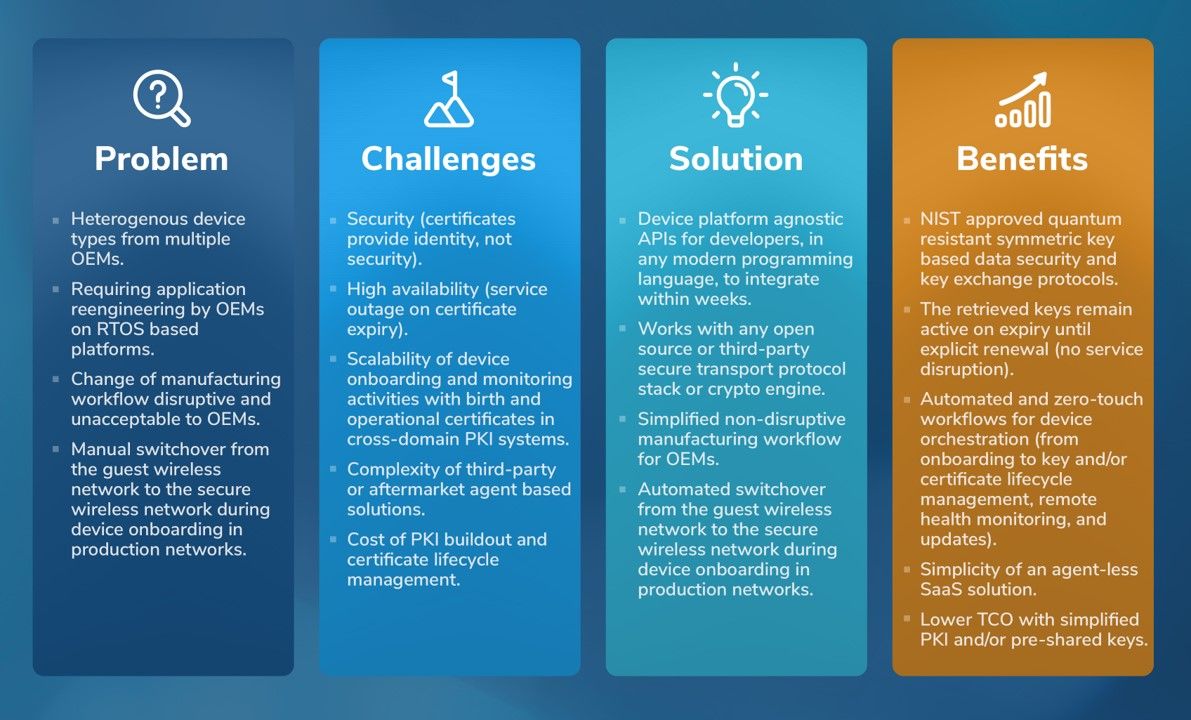
- Digital transformation requiring operational intelligence and telemetry from store equipment to analytics cloud
- Simplified asset management
- Business analytics powered by AI/ML/DS in the cloud
- Preventing unauthorized data access by third-parties
- Compliance (PCI-DSS, NIST 800)
- Secure device-to-cloud communications with authentication and data encryption
- Device and security lifecycle management
- Unified and scalable workflow for OEMs and end-user NOC/SOC/field operators
- Automated switchover from the guest to the secure wireless network during device onboarding
The market drivers for massive IoT/IIoT
The convergence of IT and OT has been challenged by the dichotomy of workflows from device onboarding to provisioning, monitoring, and in-field updates. Securing device communications (east-west, north-south) in contemporary IoT reference architectures across industry sectors, alongside network segmentation models, requires a deep understanding of methods and protocols for authentication and security. Trusted connectivity to Internet based applications and Software-as-a-Service (SaaS) platforms require domain (and cross domain) roots of trust. Post quantum risks to critical infrastructures require quantum resilience by design based on emerged standards and specifications. A cost-benefit analysis for modernization with a do-it-yourself (DIY) design that entails extensive engineering, open-source components, multi-vendor commercial off-the-shelf (COTS) components, and/or simplified APIs for low coding requires a strategic balance of technology and public/private collaborations.
Data to microservices
Data (e.g., device and application intelligence, telemetry, health metrics) to applications at the edge or in the cloud requires low latency and high bandwidth. Trusted data streams to AI/ML foundries with webhooks, for richness of training data feeds, requires labels for verifiable trust using metadata markers, signatures for data authentication, and simplicity of APIs for low coding effort on devices to instrument embedded applications.
Simplified Solution for Retailer Chains

- Use of open-source middleware (e.g., ROS, SROS, ROS-2) with no security framework for cyber physical systems (CPS)
- Network admission without authentication
- Weak messaging without integrity
- Responsibility for protection is delegated to the network intrusion detection systems external to the CPS
- Dichotomy between IT/OT/IoT poses challenges to detection models based on anomaly and threat grammar