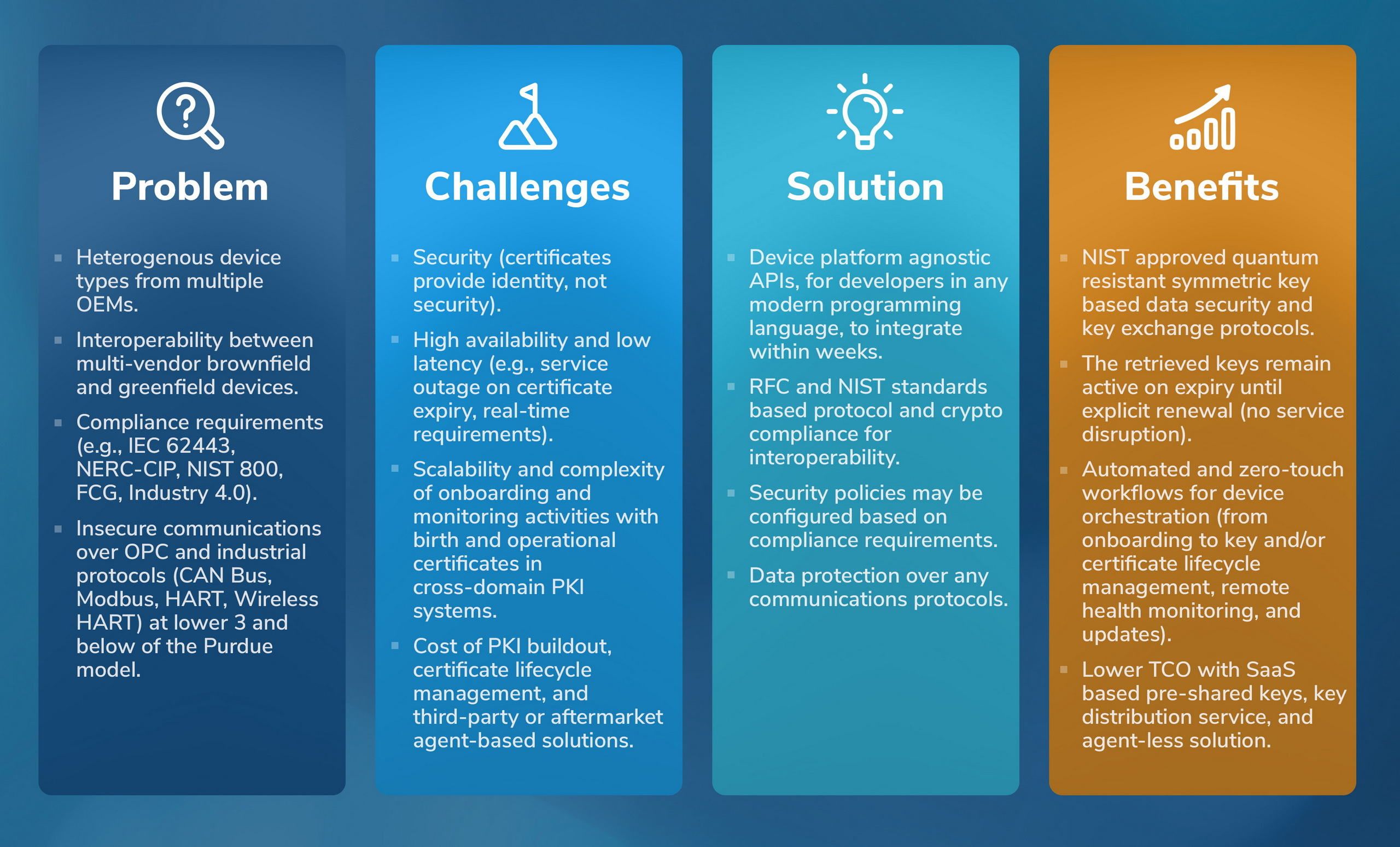
Process Automation (IIoT)
The status quo in converged Enterprise information technology (IT) and operational technology (OT) networks is physical connectivity with network level segmentation, network-based intrusion detection/prevention (IDS/IDP) predicated on insecure plaintext over-the-wire communications, or a bump-in-the-wire broker-based blockchain fabric overlay. Achieving logical trusted connectivity to implement a cost-effective and highly efficient zero-trust architecture over existing network infrastructures and in-field devices requires a paradigm shift from “cyber threats” to “cyber risks” and from “multi-layer peripheral defense” to “operational resilience at the core” for long-term desirable outcomes with application security by design.
- Digital transformation requiring operational intelligence and communications between devices (in layer 3 and lower of the Purdue model) and cloud microservices
- Simplified OT device management
- Business analytics powered by AI/ML/DS in the cloud
- Preventing attacks based on exploit of insecure communications
- Compliance (IEC 62443, NERC CIP, NIST 800, FCG, Industry 4.0)
- Secure device-to-cloud communications with authentication and encryption
- Device and security lifecycle management
- Unified and scalable workflow for NOC/SOC/DMS operators
- Interoperability between brownfield and greenfield multi-vendor devices
The market drivers for massive IoT/IIoT
The convergence of IT and OT has been challenged by the dichotomy of workflows from device onboarding to provisioning, monitoring, and in-field updates. Securing device communications (east-west, north-south) in contemporary IoT reference architectures across industry sectors, alongside network segmentation models, requires a deep understanding of methods and protocols for authentication and security. Trusted connectivity to Internet based applications and Software-as-a-Service (SaaS) platforms require domain (and cross domain) roots of trust. Post quantum risks to critical infrastructures require quantum resilience by design based on emerged standards and specifications. A cost-benefit analysis for modernization with a do-it-yourself (DIY) design that entails extensive engineering, open-source components, multi-vendor commercial off-the-shelf (COTS) components, and/or simplified APIs for low coding requires a strategic balance of technology and public/private collaborations.
Data to microservices
Data (e.g., device and application intelligence, telemetry, health metrics) to applications at the edge or in the cloud requires low latency and high bandwidth. Trusted data streams to AI/ML foundries with webhooks, for richness of training data feeds, requires labels for verifiable trust using metadata markers, signatures for data authentication, and simplicity of APIs for low coding effort on devices to instrument embedded applications.
Unified Reference Architecture
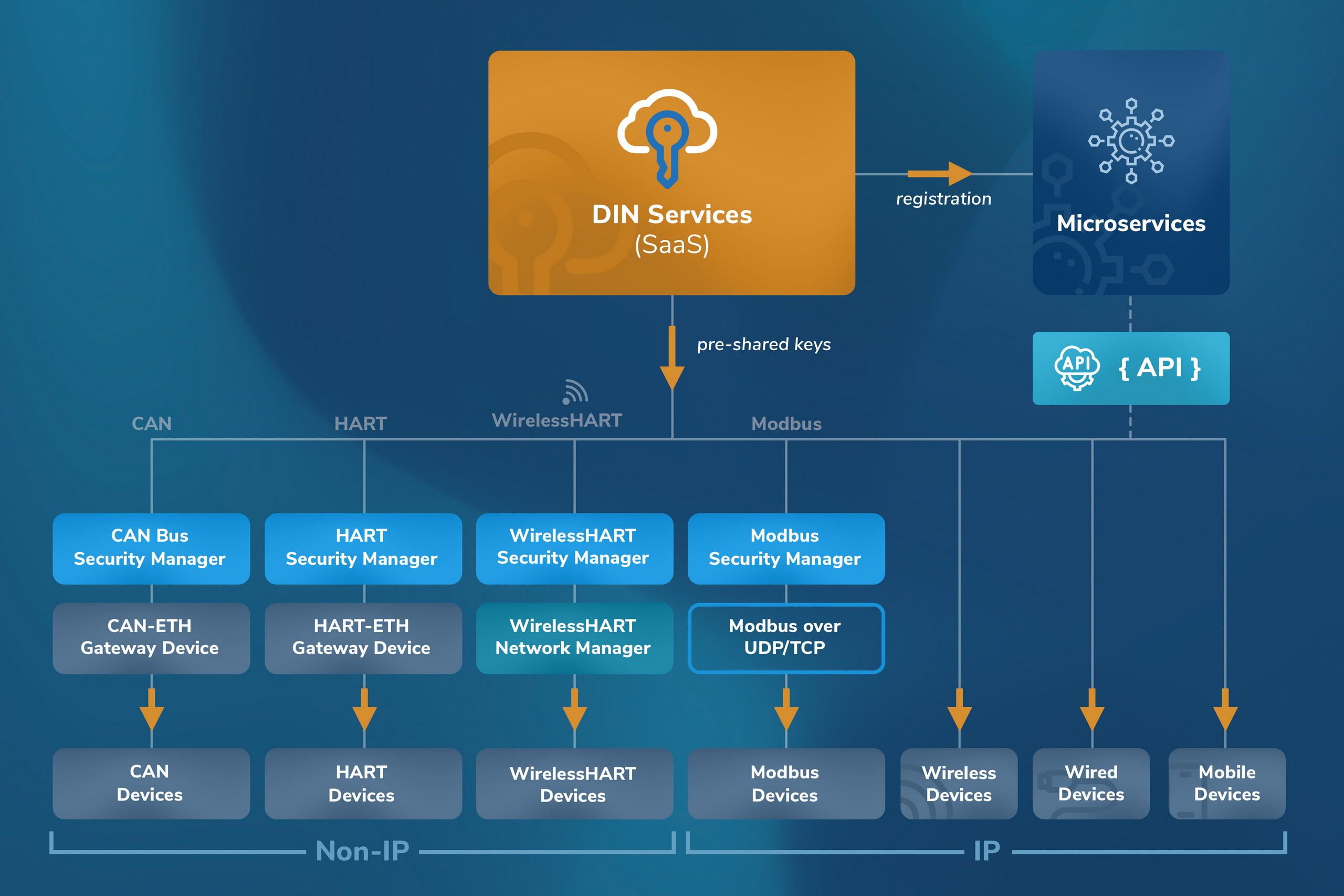
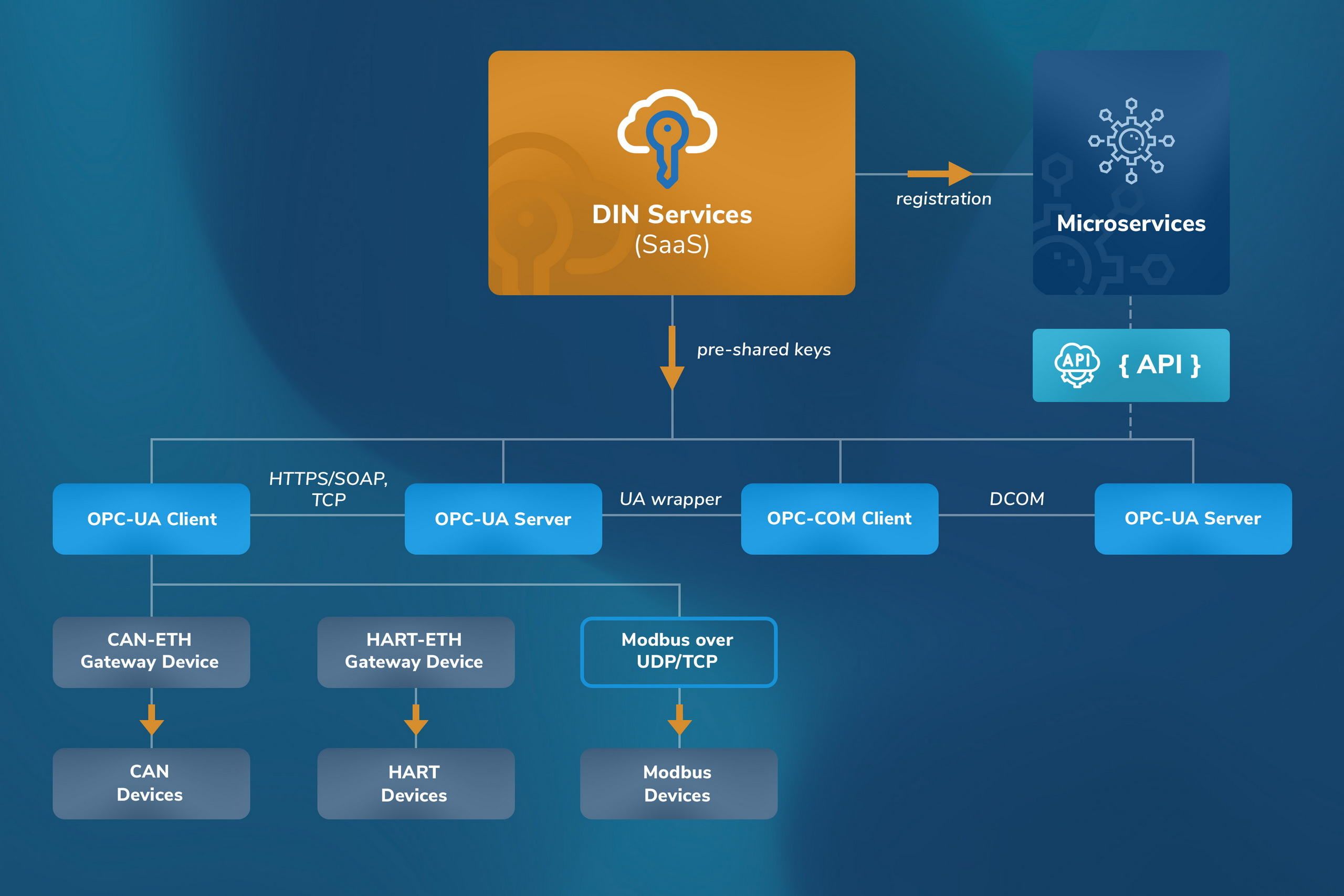
Industrial control protocols (e.g., HART, Modbus, Foundation Fieldbus, Serial) are highly effective in closed environments (but not immune to message injection) and require hardening within the scope of the message frames to transmit non-repudiable message integrity/authentication codes. Cloud access protocols, namely publish-subscribe protocols (e.g., MQTT, AMQP) over secure transport protocols (e.g., TLS, HTTPS), require extensive coding for registration, authentication ceremonies, and data exchange.
Local area networks (LANs) intrinsically operate as a single domain of trust. Air-gapped devices operate within closed networks and require on-premises automation and workflows. Local authentication establishes non-transitive trust on the first mile only. Establishing a wider network outreach with cross-domain trust requires use of security tokens to integrate with collaborative services over wide area network (WAN) service hubs and buses.
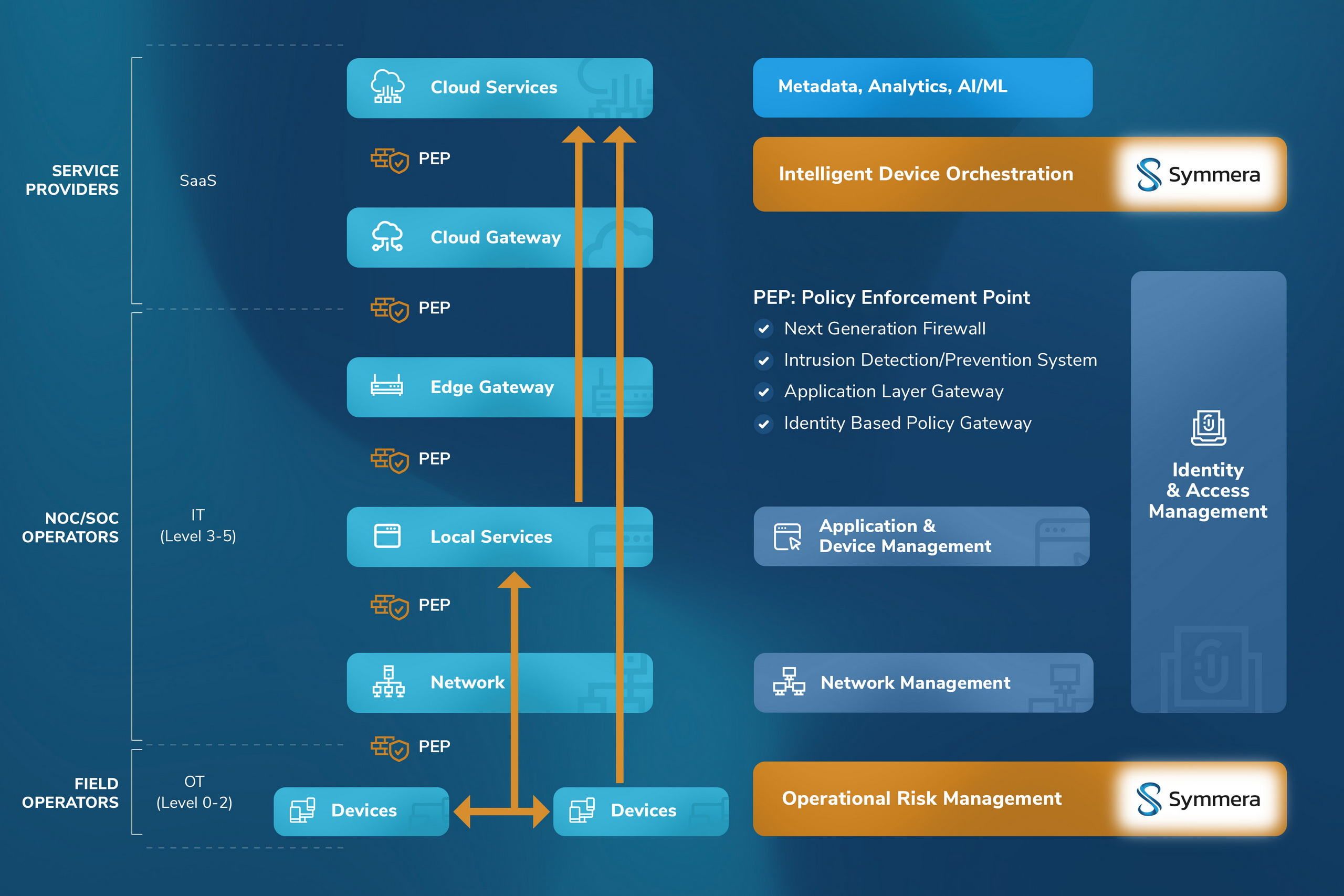
Data is the new oil. This is the information technology era paradigm of “data to data lake”, “data to policy”, or “data to process”. In operational technologies (IoT/IIoT) the emerging new paradigm is “data to AI/ML”. Further, in air-gapped and controlled environments (e.g., Purdue models in industrial control systems) on-premises platforms are preferred over on-cloud SaaS platforms.