Technology
- Operational Risk Management in the Post Quantum Era
- Reference Architecture for Intelligent Device Orchestration
- Certificate Based Security for Lightweight PKI (Simplified)
- Platform Orchestration for Massive IoT/IIoT
- Key Based Security for Zero PKI (Quantum Proof)
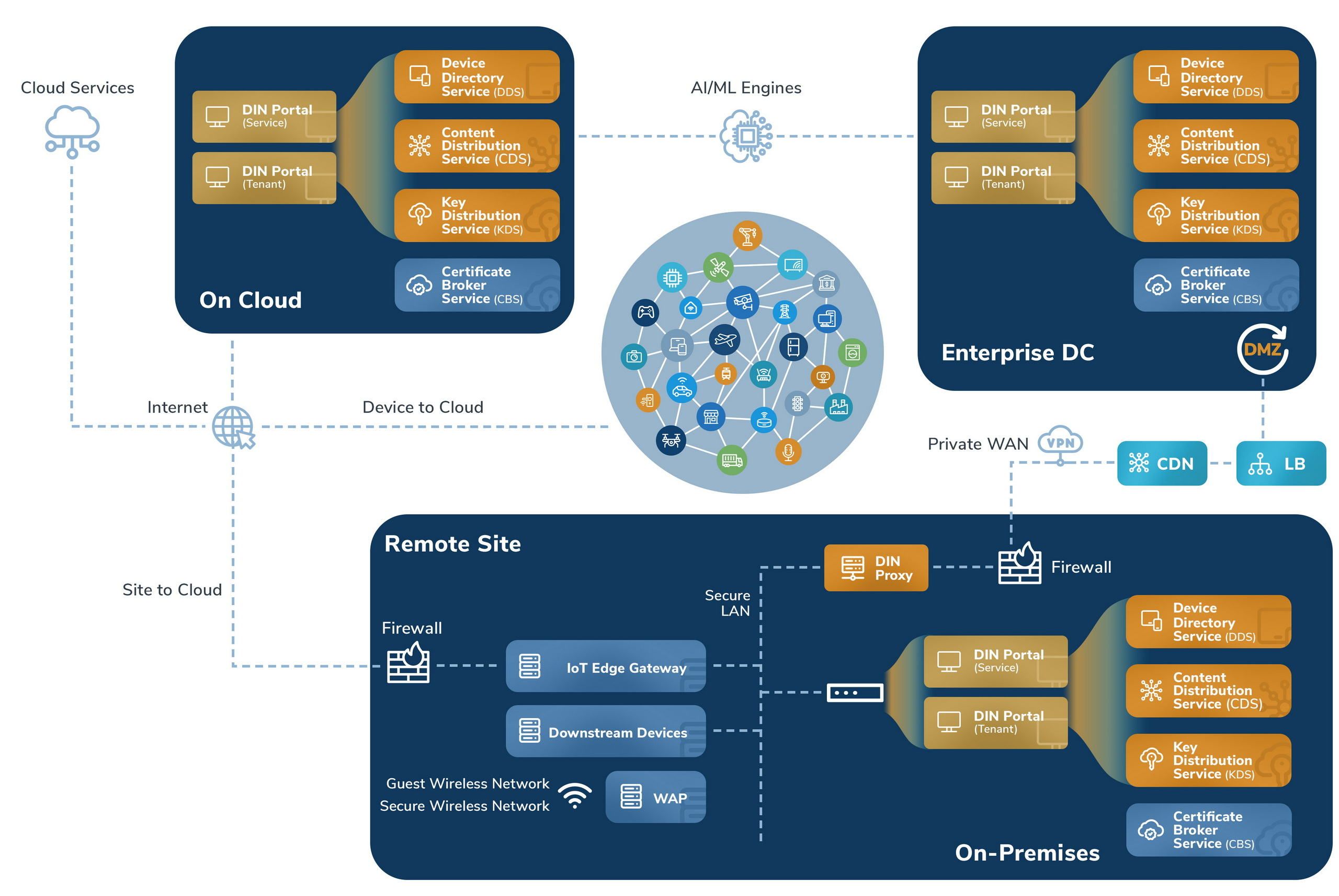
- On-Cloud or On-Premises SaaS Deployment Models
- Device Directory Service
- Content Distribution Service
Operational Risk Management in the Post Quantum Era
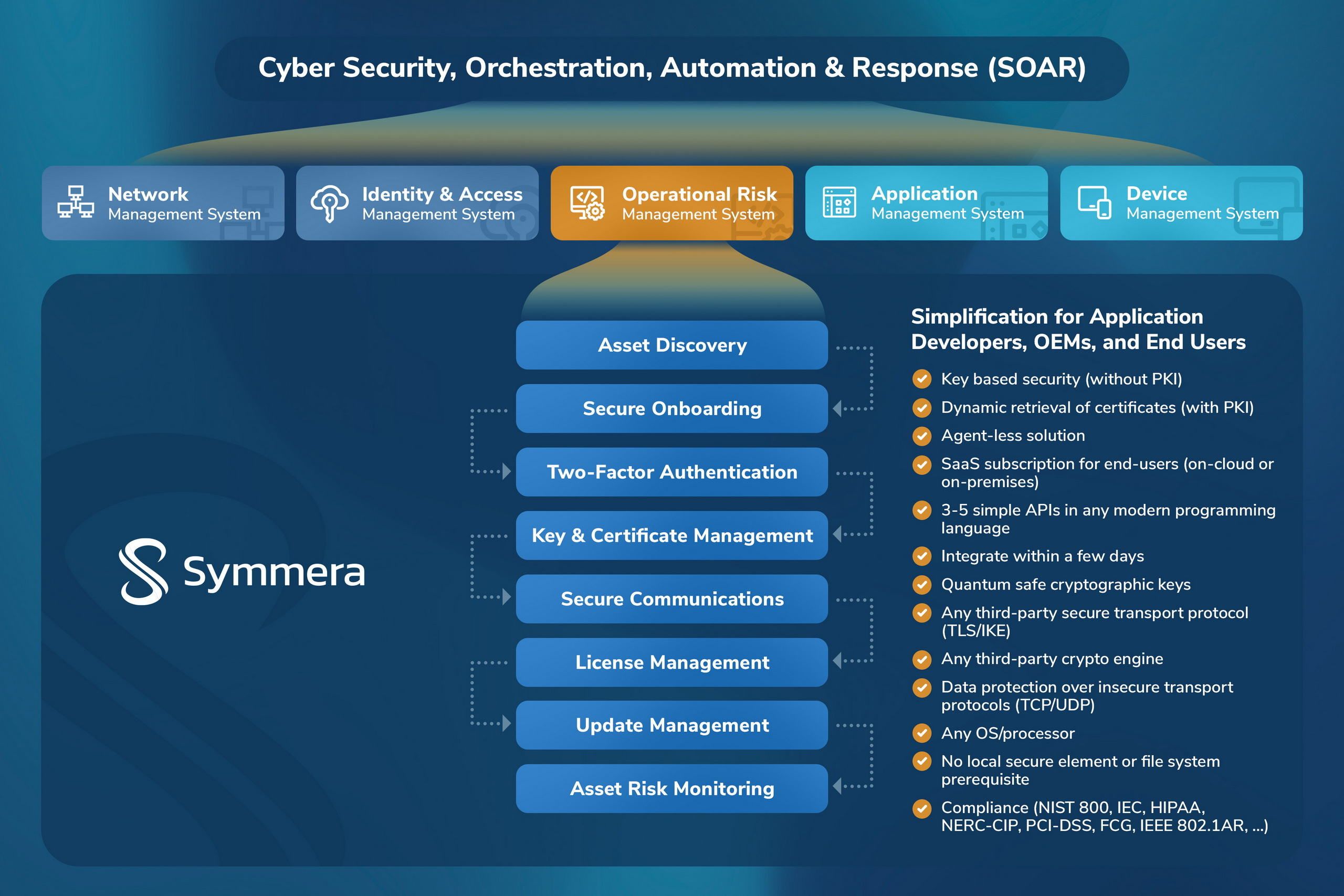
The lack of visibility and control of operational technology (OT) devices to traditional information technology (IT) network and security operations center (NOC/SOC) operators poses major risks to digital transformation initiatives and IT-OT convergence.
The solution provides a cost-effective, automated, and scalable symmetric pre-shared key distribution service for private (Enterprise, Tactical) and public (Internet) networks; permissioned group membership for devices with DNS domain or Mobile Service Provider (MSP) validation; simplifies key generation, distribution, and management; and eliminates complicated certificate provisioning, key renewal, and key/certificate lifecycle management workflows. The agent-less solution protects devices in IoT, IIoT, and OT environments with application security by design to authenticate and communicate securely with data integrity and confidentiality, without requiring expensive PKI based digital certificates for every device, and/or complicated key and certificate lifecycle management services from certificate authorities.
Distributed Intelligent Network (DIN) is defined as critical application, data, and infrastructure elements that reside outside of the traditional Data Center or Enterprise premise location. This would include Intelligent Edge for Analytics/AI applications, Autonomous Machines (robotics, drones, vehicles), 5G mobile network & applications, Smart buildings and energy, Distributed Energy systems (grid, solar, utilities, pipelines), Industrial controls, and the Internet of Things (IoT). As intelligence continues to move outside of traditional Data Centers, it becomes exponentially more vulnerable to attacks. The security paradigm needs to shift from connectivity to provenance and trust in data.
The DIN orchestration platform provides a secure, highly available, and scalable suite of services for:
- Device discovery and onboarding
- Quantum-safe key distribution and lifecycle management
- Certificate distribution and lifecycle management
- Content distribution with supply chain tamper resistance and attestation of content inspection
- Device metadata harvesting and forwarding to third-party services (e.g., AI/ML/SIEM/SCADA)
Reference Architecture for Intelligent Device Orchestration
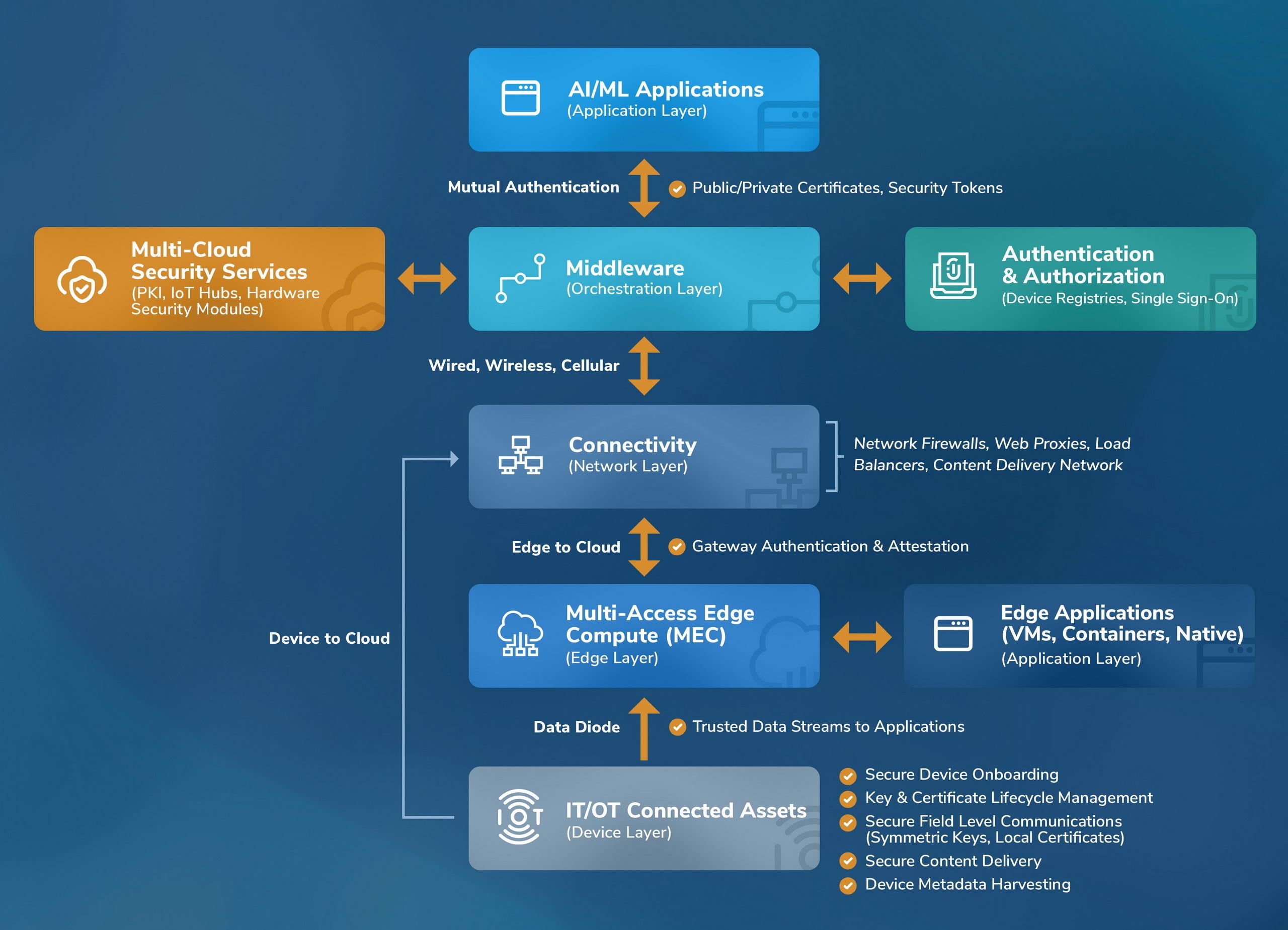
IoT solutions are a synergistic confluence of three distinctive platforms: Cloud, Orchestration, and Application (Edge, AI/ML). The IoT reference architecture for connected cyber physical systems comprises of the device layer, edge layer, network layer, orchestration layer, and the (edge, AI/ML) application layer. The orchestration layer is the core component to simplify east-west APIs for lateral integration with collaboration services, north-bound APIs for trusted connect to applications, and south-bound APIs for device orchestration. Choosing a cloud platform is a decision to opt for vendor lock-in or factor in multi-cloud agility. The selection of a proprietary or cloud agnostic middleware APIs is consequential for long-lived devices and/or applications and future cloud platform migration considerations.
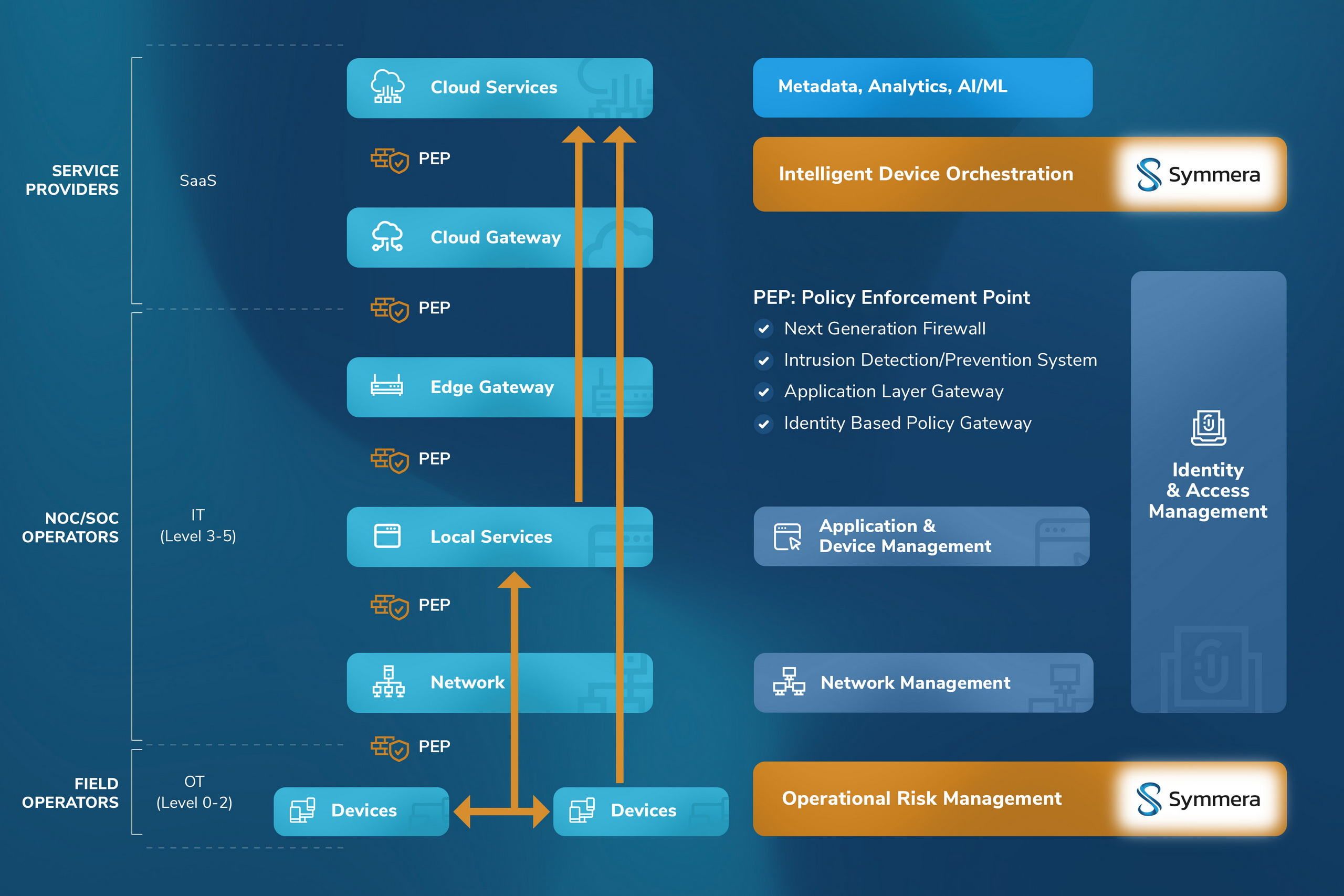
Data is the new oil. This is the information technology era paradigm of “data to data lake”, “data to policy”, or “data to process”. In operational technologies (IoT/IIoT) the emerging new paradigm is “data to AI/ML”. Further, in air-gapped and controlled environments (e.g., Purdue models in industrial control systems) on-premises platforms are preferred over on-cloud SaaS platforms.
Certificate Based Security for Lightweight PKI (Simplified)
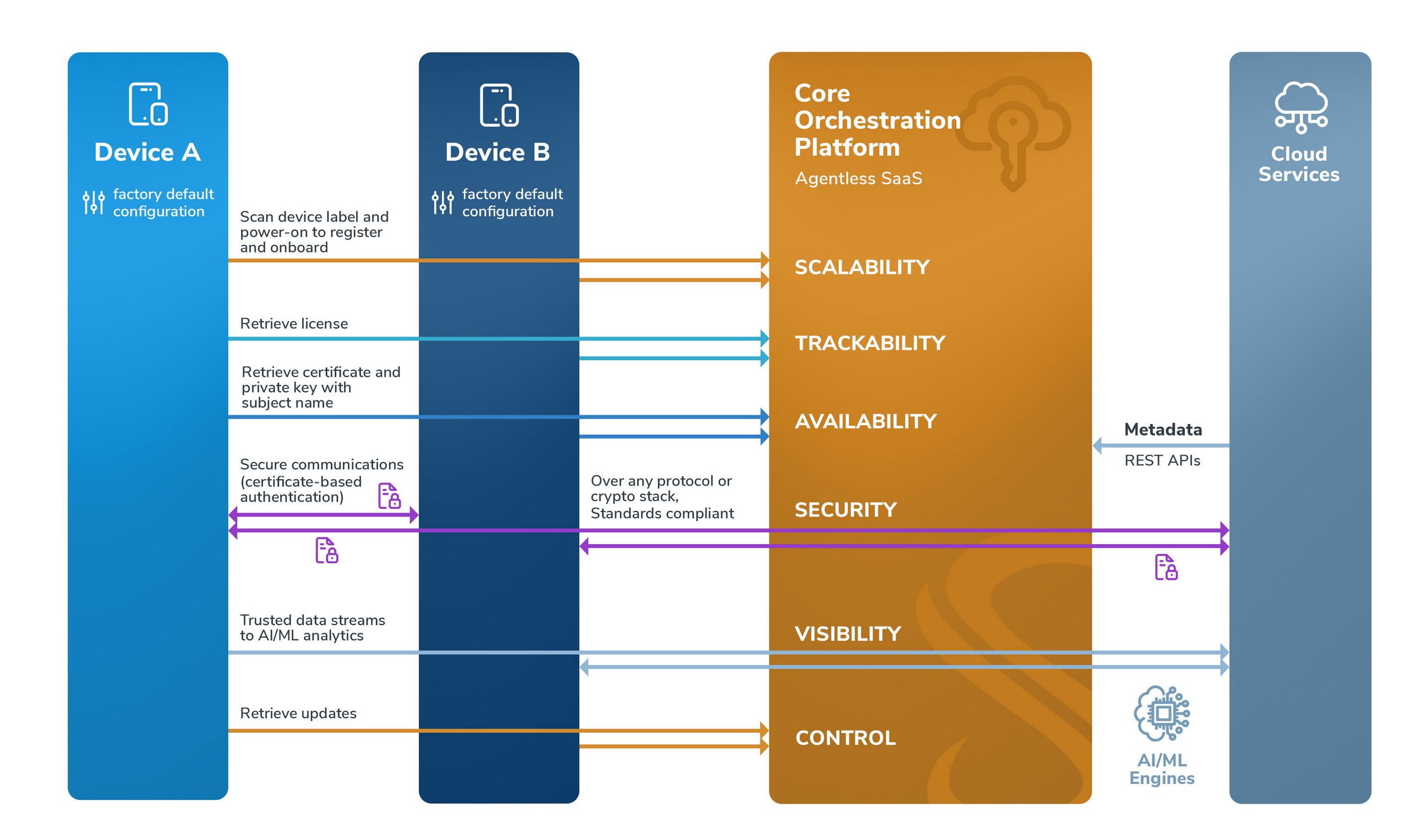
Symmera’s certificate broker service supports certificate-based authentication with:
- Quantum proof cryptography on existing infrastructures with two-factor device authentication and group permissions based secure channel for certificate and private key distribution
- Automated high velocity or on-demand key rotation with dynamic retrieval of keys and certificates (without requiring local secure element on device) or secure export to local persistent store (with device unique key)
- Simplified and lightweight PKI with a broker service for trusted CA certificates, and automated key and certificate lifecycle management
- Zero PKI with fully managed self-signed local certificates with security extensions (host address or network subnet) for runtime verification, authentication, and authorization in controlled (closed, air-gapped) environments
- High availability with service level failover
- Flexibility with an on-premise virtual appliance or on-cloud hosted service and on-premise proxy option
The solution reference architecture for device orchestration varies based on the building blocks to implement a zero-trust model. Symmera’s DIN services support use of public key infrastructure for device certificates with highly simplified APIs (in any programming language) without requiring implementation of complex key and certificate management protocols and authentication methods on autonomous device platforms.
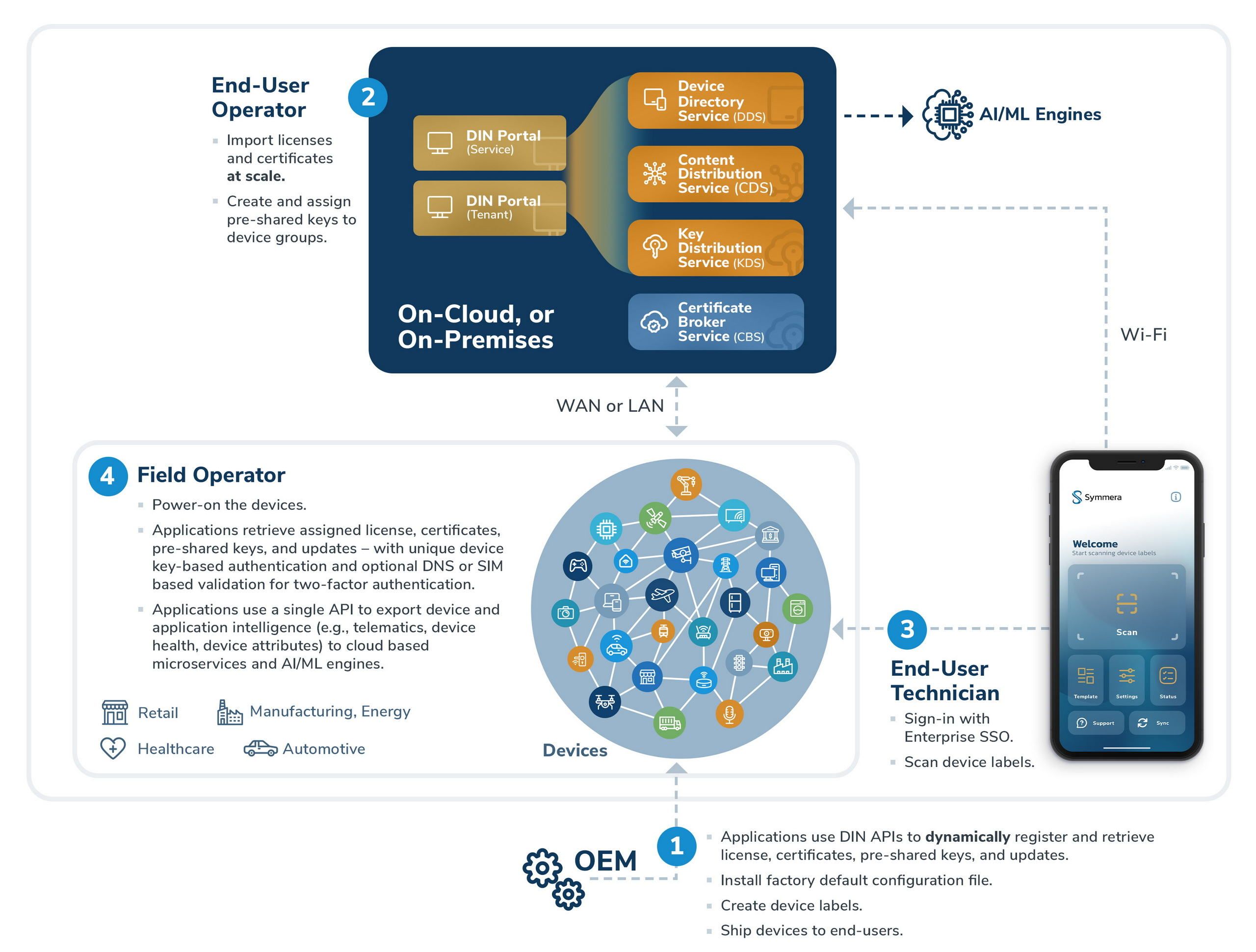
- A factory default configuration based on device type is generated by the service tenant (or end-user) and installed on devices during manufacture or in the field. The field operator authenticates with SSO and scans the device label using the Symmera Device Onboarder Mobile App for credentialing. A device license and certificate based on the discovered IEEE 802.1ar compliant device identifiers is automatically assigned to the device. At first-time power-on the device is registered and onboarded, using an API or command line utility. This zero-touch provisioning method provides scalability to onboard devices at scale without human errors. All service requests to the orchestration platform require device two-factor authentication, with a configurable option for single-factor authentication based on the operational network environment.
- Applications on the device can retrieve an OEM issued license using a single API or command line utility.
- Applications can retrieve trusted certificates, and device or application certificates with the associated private key by subject name, dynamically on-demand over a secure channel and verify certificate status using APIs in any modern programming language. The private key can optionally be stored on a local secure element – such as a TPM or SIM, or encrypted using a software based PUF. In the absence of a local secure element or writable file system on the device, the certificate and private key can be retrieved on-demand and not stored locally.
- The device can now authenticate using a certificate for peer-to-peer communications with other devices or services hosted on-premises or on-cloud over any secure transport protocol stack such as TLS, SSH, IPsec/IKE, or EAP, and with any cryptographic engine such as a third-party FIPS compliant or quantum-safe library.
- Applications can send trusted data streams such as telematics, device attributes, or operational measurements for visibility and remote monitoring, using a single API to cloud services for AI/ML based data analytics.
- Devices can retrieve updates published by OEMs and after-market application vendors with supply chain provenance and apply updates without modifications to platform specific update methods for control and remote remediation.
- Device metadata can also be ingested using authenticated REST APIs by collaboration services such as SIEM and AI/ML engines for risk monitoring, data analytics, and training models.
Key Based Security for Zero PKI (Quantum Proof)
Key Distribution Service
- Key distribution and lifecycle management for private and shared symmetric keys.
- Quantum-safe, NIST approved, key exchange methods.
- Device two-factor authentication.
- Key based application security with visibility and control for operational risk assessments.
- Simple (3-5) library APIs in polyglot languages (C, C+, C#, Java, Go, Rust) for developers to harden applications in a few days.
- Holistic protection (client authentication, data authentication, and data encryption) over any transport protocol stack (TLS, IKE, UDP, TCP) and with any cryptography engine.
- Works on resource constrained and resource slack brownfield and greenfield devices.
- No PKI buildout or device certificates required.
- Significant simplification for OEMs and application developers.
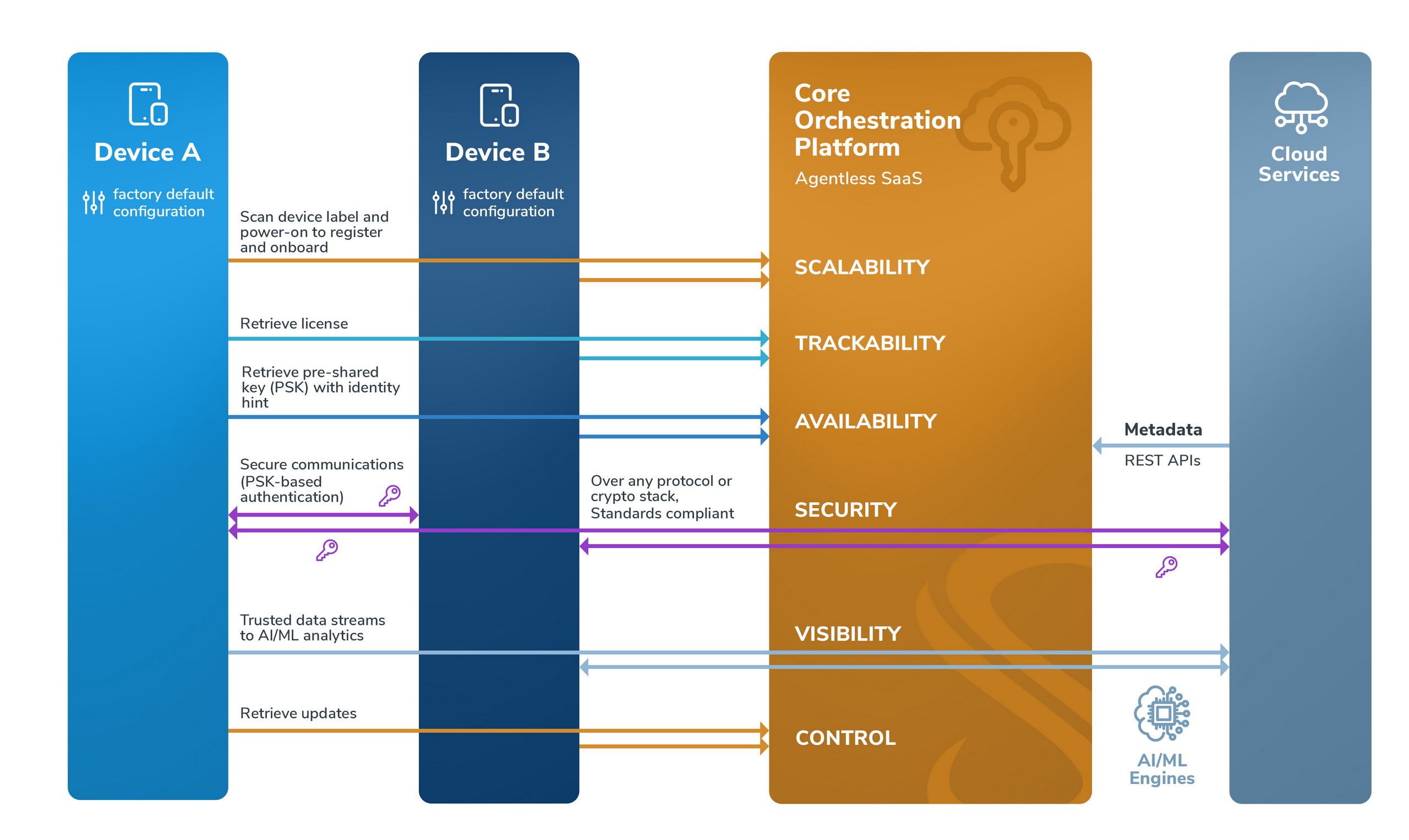
Symmera’s key distribution service supports pre-shared symmetric key-based authentication with:
- Quantum proof cryptography on existing infrastructures with two-factor device authentication and group permissions based secure channel for symmetric key distribution
- Automated high velocity or on-demand key rotation with dynamic retrieval of keys and certificates (without requiring local secure element on device) or secure export to local persistent store (with device unique key)
- Quantum proof symmetric keys for device authentication over secure transport protocols, and data protection over insecure transport and industrial protocols
- High availability with service level failover
- Flexibility with an on-premise virtual appliance or on-cloud hosted service and on-premise proxy option
The workflow for symmetric key-based authentication is identical compared to certificate-based authentication.
In closed environments, with air-gapped or offline devices, use of symmetric keys is recommended to achieve security, availability and scalability. Besides, use of symmetric keys requires no PKI buildout which reduces the total cost of ownership and overcomes common challenges associated with use of certificates on autonomous OT devices – namely hybrid PKI systems, service disruption due to certificate expiry, memory constraints that impose limitations on certificate and certificate chain sizes, and restrict use of large certificates with multi-signature schemes for post quantum ciphers.
Applications can retrieve pre-shared keys with an identity hint, dynamically on-demand over a secure channel, using APIs in any modern programming language. Use of pre-shared keys for client authentication with secure transport protocols such as TLS, IPsec/IKE, and EAP are described in the respective RFC standards. The retrieved symmetric key can, optionally, be stored on a local secure element – such as a TPM or SIM, or encrypted using a software based PUF. In the absence of a local secure element or writable file system on the device, the key can be retrieved on-demand and not stored locally.
Device Directory Service (Asset Metadata)
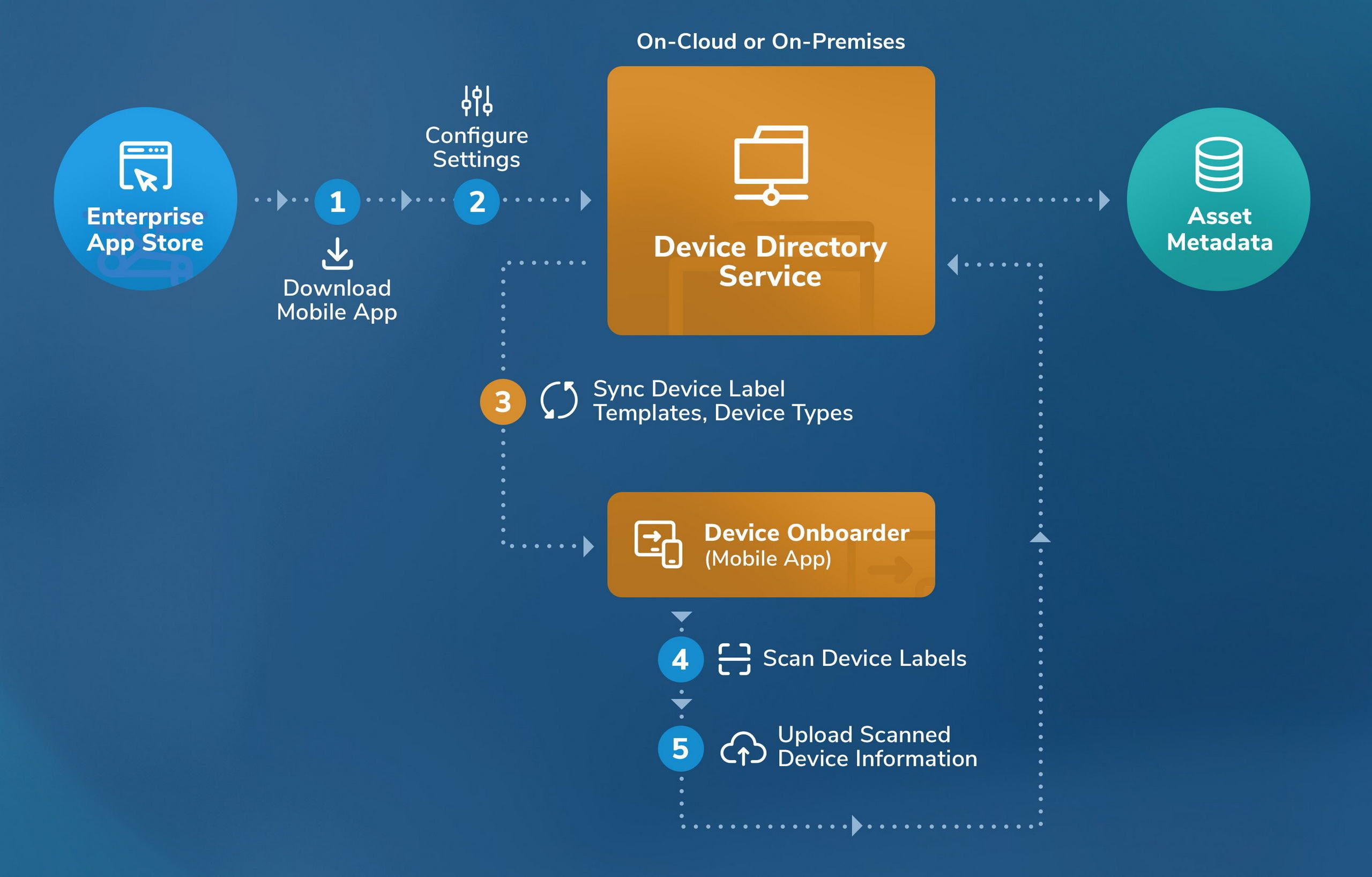
Device Directory Service (DDS)
- Device label scan-based device discovery with device identifiers from text, bar codes, and QR codes on printed device labels.
- Zero-touch device onboarding.
- Authoritative device information for contextual risk monitoring.
- Simple (3-5) library APIs in polyglot languages (C, C+, C#, Java, Go, Objective-C, Swift, Rust) for efficient and extensible device telematics on RTOS and GPOS platforms.
- Rich and trusted asset metadata to prime AI/ML training models for cyber risk assessment and timely mitigation.
- Significant operational efficiencies and cost savings for OEMs and end-users.
Content Distribution Service
(Trusted Updates Over-the-Air/Network)
Trusted Content Distribution (with Signature Manifest)
-
The code signing may be performed from the tenant portal using the configured code signing service provider.
-
Uses symmetric key based multi-party content signing by the producer and one or more brokers, and multi-person digital signing.
-
The digital signing (symmetric) keys are retrieved out-of-band over a secure channel (in split mode, wherein the keys are not transmitted along-side signed content). The split mode comprises of a first secure channel for two-factor user and device authentication-based creation and retrieval of a plurality of digital signing symmetric keys, and a second secure channel for content distribution (e.g., content file, signature manifest file).
-
Requires device two-factor authentication for content retrieval (without requiring PKI or device certificates).
-
Gated workflow sequence based multi-part content inspection, notification-based approval, and notification-based publishing with role-based separation of duties and multi-person digital signing rule (with at least 4-person digital signing recommended).
-
The content approval is content inspection-based (and not merely based on the user’s role and privileges).
-
The external third-party content inspection method (e.g., static analysis, dynamic analysis, sandboxing, anomaly detection, reputation lists) is based on the approver’s security profile and threat model assessments.
-
The authorized download URL/URIs are retrieved by the OEM application with device two-factor authentication from the KDS (i.e., not embedded at factory in the OEM’s application) and may be hosted in the controlled environment of the device owner/operator.
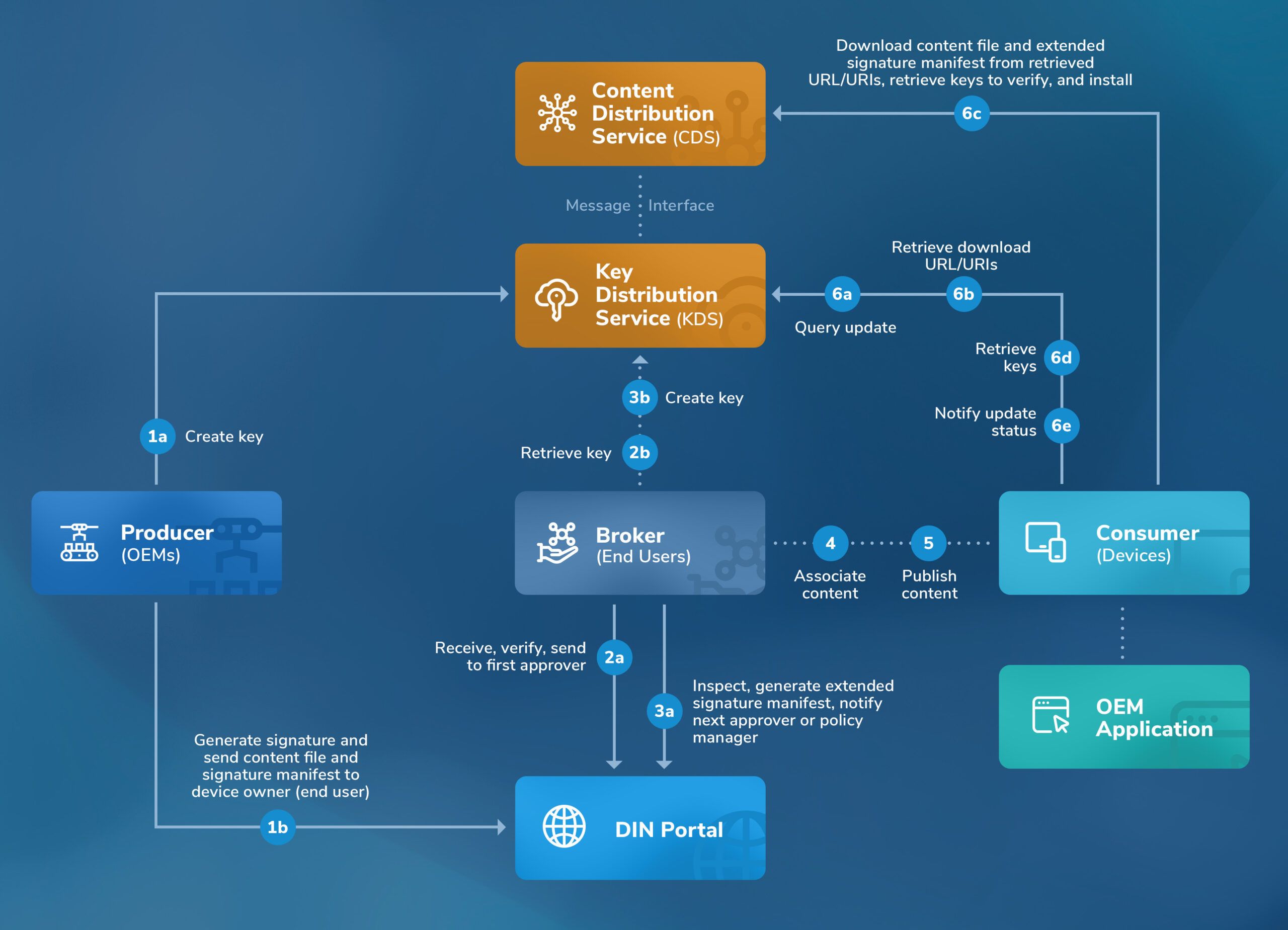
Simplified Content Distribution (with Gated Workflow)
- Content distribution with supply chain tamper resistance.
- Secure content distribution with multi-person rule-based digital signing, content inspection, and approval chain.
- Gated workflow for multi-stage content inspection (e.g., static analysis, dynamic analysis, sandboxing, anomaly detection, reputation lists).
- Split-mode secure channels with user and device two-factor authentication for content retrieval and key operations.
- Symmetric key based digital signing (no PKI, asymmetric keys, or certificates required).
- Simple (3-5) library APIs in polyglot languages (C, C+, C#, Java, Go, Rust) for applications to check for updates, securely download, and apply.
- Trusted device updates with visibility for end-to-end supply chain risk monitoring.
- Significant simplification of device management for OEMs and end-users.