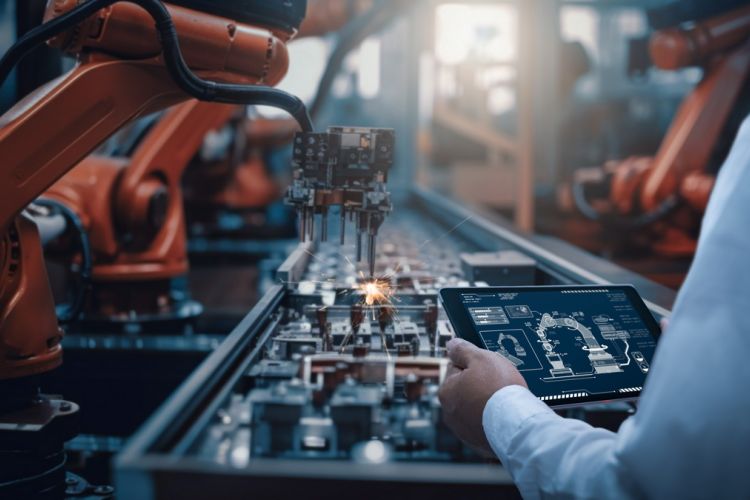
XIoT + AI/ML Simplified
We help application developers, device manufacturers, and end-users empower AI/ML engines with cyber safe devices and trusted data
-
Enabling device two-factor authentication with trusted identifiers on existing infrastructures
-
Achieving scalability, high availability, and security with quantum proof cryptography
-
Harvesting trusted data streams to empower AI/ML today – with device and application intelligence, AI risk classification, and data labels
-
Next generation of digital trust in connected devices and services – with simplified APIs for embedded trust, and without complex protocols for key and certificate management
Symmera’s simplified agentless APIs for application developers to integrate with our distributed intelligent network orchestration platform for massive AI/ML enablement, and our on-cloud or on-premises SaaS platform for flexible deployment, unified IT/OT workflows, and operational efficiencies have been verified with security protocol stacks, crypto libraries, PKI systems, authentication services, and cloud IoT platforms from top vendors.







WHAT WE DO
We enable secure field communications and trusted data streams from devices to microservices.
Enabling Operational Risk Management with a SaaS Platform
-
Simple APIs for device and data protection in any programming language
-
Workflow automation for application development and factory provisioning of IoT/IIoT devices at scale
-
Zero-touch onboarding with device label scan for operational efficiency
-
Secure field level communications with quantum proof cryptography and standards-based interoperability
-
Trusted content distribution to field devices over-the-air/wire with supply chain tamper resistance and policy based secure updates
-
Securely published trusted device and application intelligence (metadata) to microservices for data analytics by AI/ML engines at the edge or on-cloud
Benefits for Developers, OEMs, and End-Users
Benefits for Developers, OEMs, and End-Users
10-factor simplification of APIs and end-to-end workflows for operational efficiencies from factory to field.
-
Only 23 APIs in any programming language (instead of 500+ service provider specific APIs, complicated certificate and key management protocols, and authentication ceremonies)
-
Application integration within days on any device platform
-
Works with any open-source or third-party secure transport protocol or crypto library
-
Onboard devices at scale using a Mobile App to scan device labels
-
Quantum proof symmetric keys for device authentication over secure transport protocols, and data protection over insecure transport and industrial protocols
-
Automated lookup and assignment of device licenses and certificates – with policy based high velocity rotation of keys and certificates
-
Secure distribution of managed content with code signing, detached multi-signature manifest, update policies, and distributed content stores for scalability
-
Gated workflows with multi-person rules
-
Notifications based authorization and approval for audit trail
Why choose our digitalization platform for device to AI/ML solutions?
HOW IT WORKS
Flexible deployment and configuration for fit-and-finish in site infrastructures
with online or air-gapped devices.
Deploy as an On-Premises or
On-Cloud SaaS Platform
-
Quantum proof cryptography on existing infrastructures with two-factor device authentication and group permissions based secure channel for symmetric or asymmetric key distribution
-
Automated high velocity or on-demand key rotation with dynamic retrieval of keys and certificates (without requiring local secure element on device) or secure export to local persistent store (with device unique key)
-
Simplified and lightweight PKI with a broker service for on-demand trusted CA issued certificates, managed pool of keys and certificates, and automated key and certificate lifecycle management
-
Zero PKI with fully managed self-signed local certificates with security extensions (host address or network subnet) for runtime verification, authentication, and authorization in controlled (closed, air-gapped) environments
-
Segmentation with a single or multi tenant hosted architecture (private and group-based encryption domains)
-
Single sign-on for user authentication and role-based access controls
-
High availability with service level failover
-
Key vault for key protection
-
Metadata repository with a database cluster for replication and long-term retention
-
Flexibility with an on-premise virtual appliance or on-cloud hosted service and on-premise proxy option
Benefits for Developers, OEMs, and End-Users
Simplified Solution for IT/OT Convergence
Scalability
- Agentless
- Just 3-5 APIs
- Speed to market
- Any device type
Availability
- No service disruptions
- Ubiquitous
Security
- Standards compliant
- Full interoperability
- Zero or lightweight PKI
- Quantum resistant
Trackability
- Automated management
- Remote asset management
Metadata
- One API to export device and application intelligence
Contact us
Schedule a meetup or send us your question
-
info@symmera.com
-
1941 Pearl Street
Suite 200, Boulder
CO 80302