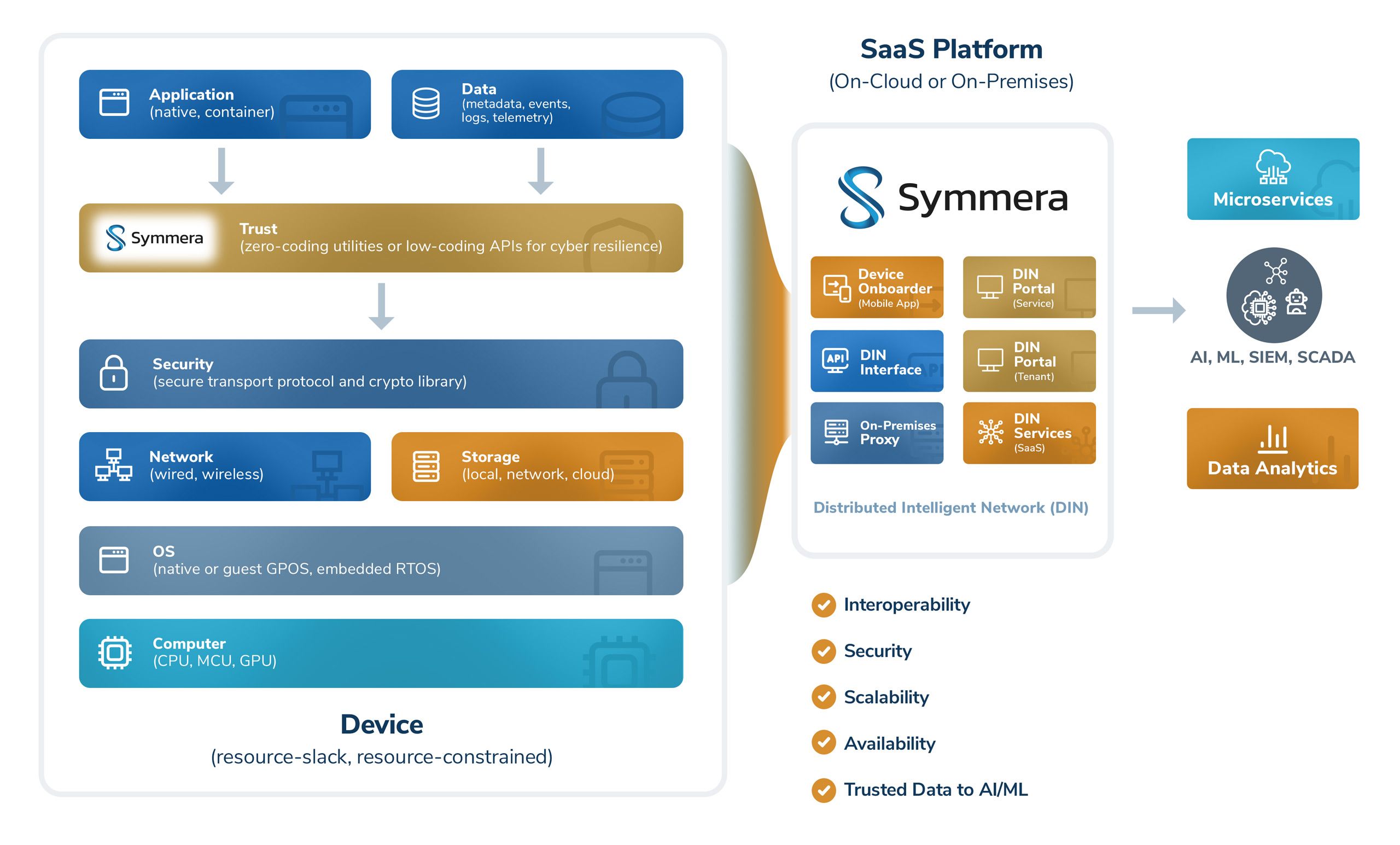
Simplified IT/OT Convergence at Scale
The convergence of IT and OT has been challenged by the dichotomy of workflows from device onboarding to provisioning, monitoring, and in-field updates. Securing device communications (east-west, north-south) in contemporary IoT reference architectures across industry sectors, alongside network segmentation models, requires a deep understanding of methods and protocols for authentication and security. Trusted connectivity to Internet based applications and Software-as-a-Service (SaaS) platforms require domain (and cross domain) roots of trust. Post quantum risks to critical infrastructures require quantum resilience by design based on emerged standards and specifications. A cost-benefit analysis for modernization with a do-it-yourself (DIY) design that entails extensive engineering, open-source components, multi-vendor commercial off-the-shelf (COTS) components, and/or simplified APIs for low coding requires a strategic balance of technology and public/private collaborations.
Simplified Factory to Field Workflows
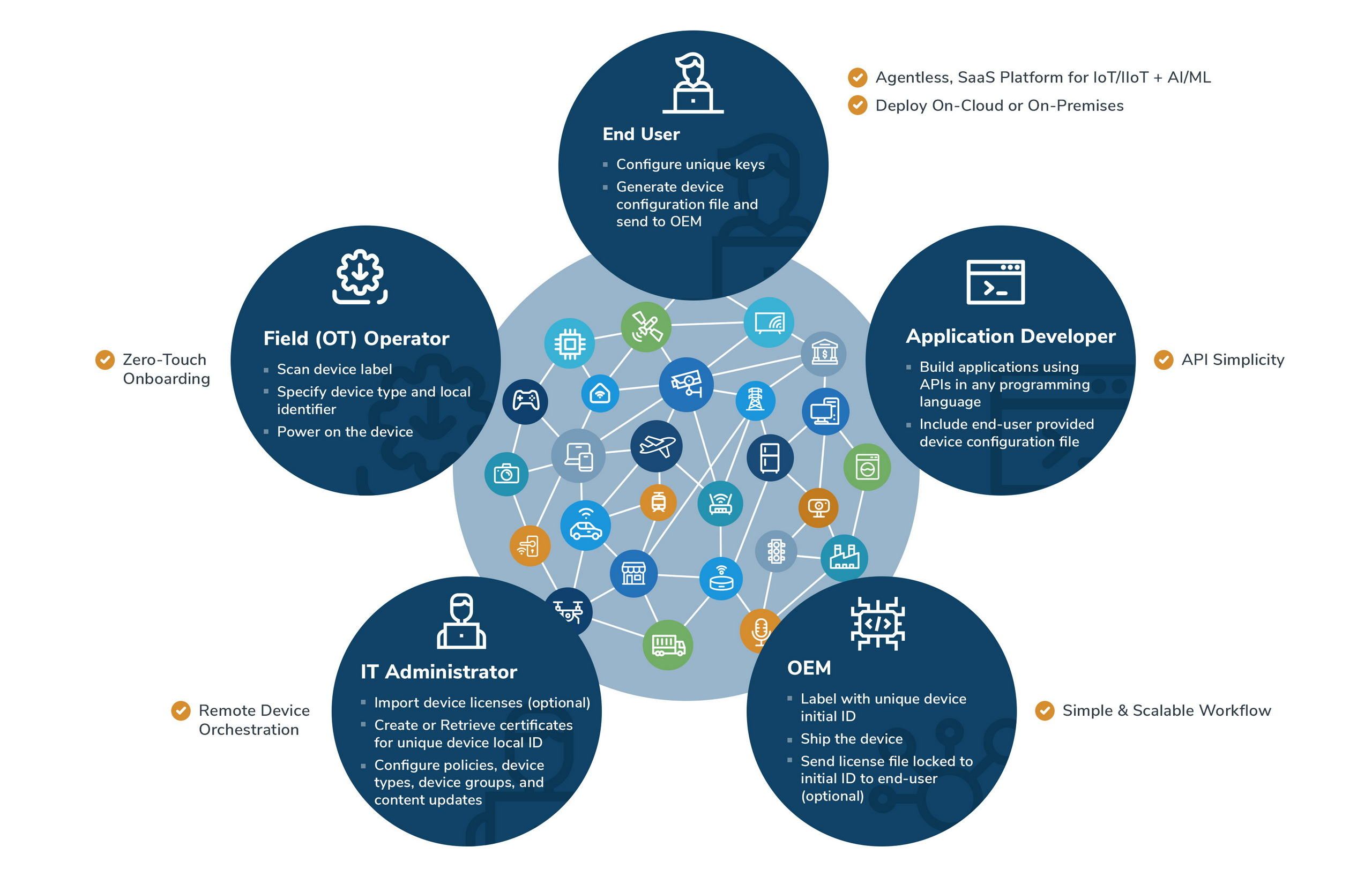
The dichotomy between information technology (IT) and operational technology (OT) workflows, the heterogeneous nature of device platforms, and cloud-platform lock-in (i.e., lack of multi-cloud APIs) poses challenges to all stakeholders in IoT/IIoT. With massive investments in AI/ML, the cloud IoT platforms require a ubiquitous client interface for autonomous devices, analogous to web browsers that serve as universal user agents for web services. Empowering application developers, OEMs and end-users requires massive simplification of APIs for application developers, accelerated workflows for OEMs, and device orchestration for end-users. Without a simplified and unified workflow, the diversity of IT and OT workflows will require extensive NOC/SOC operator re-training.
Intelligent Orchestration of Things
-
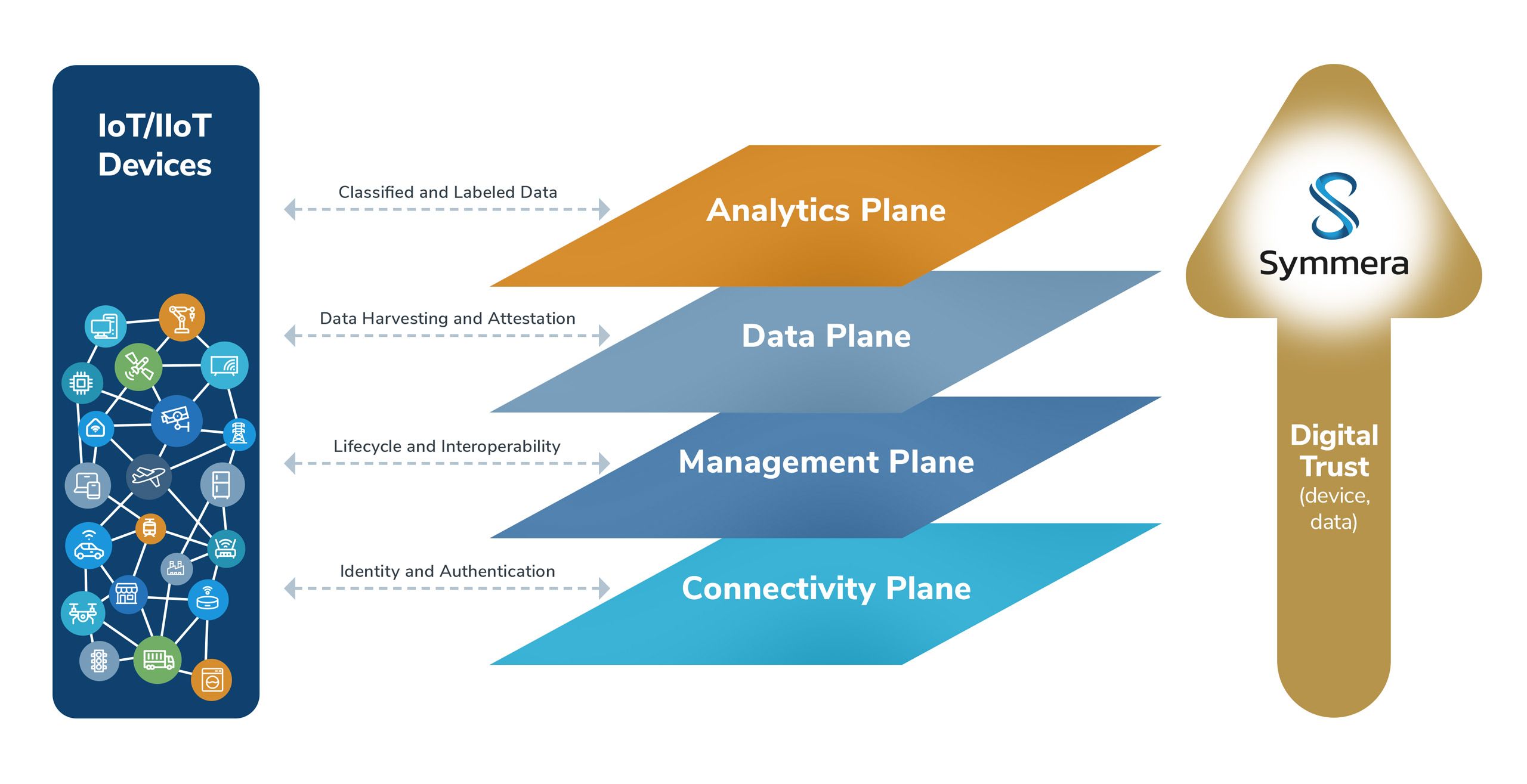
Device credentialing for asset identification and activation.
-
Device authentication for access and authorization controls
-
Secure communications for key exchange and data confidentiality.
-
Data signing for data attestation.
-
Data attestation for trusted data (with deep-fake and tamper evidence detection).
-
Trusted data to AI/ML powered by intelligent device orchestration.

Digital transformation of devices in operational technologies to leverage cloud services, artificial intelligence, and machine learning for operational efficiencies and cost reduction requires intelligent device orchestration. Using current approaches, this will require a long tail engineering development cycle for software design, interoperability testing, functional regression, field updates for reconfiguration, and operator training because of the dichotomy between IT and OT workflows. Symmera’s agentless multi-tenant SaaS platform addresses the core elements of intelligent device orchestration.
Simplification from Developers to Operators
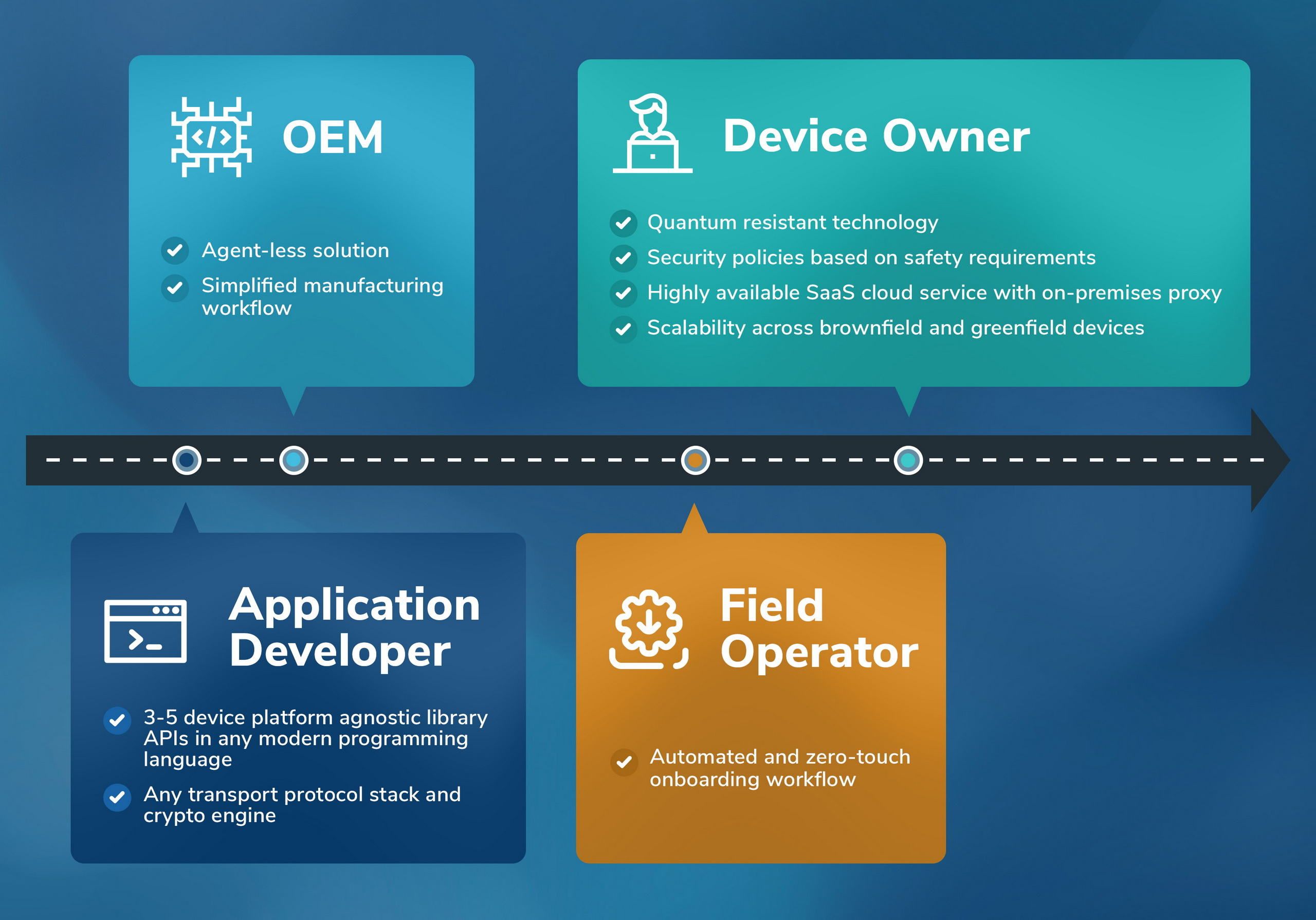
-
Device Manufacturers
Device manufacturers, owners, and operators face production, operational, and economic challenges due to workflow dependencies on public/private PKI systems, high recurring costs of certificates issued by a commercial certificate authority (CA), emerging post quantum threats to asymmetric keys and PKI systems, and the complexity of in-field device key and certificate lifecycle management. Provisioning manufacturer issued birth certificates on devices during manufacturing in air-gapped and controlled environments poses scalability and workflow challenges at the factory. Provisioning owner issued operational certificates on devices during on-boarding poses scalability and workflow challenges in the field. The nature of split and/or heterogeneous PKI systems between the original equipment manufacturer (OEM) and device owner/operator poses cross-PKI interoperability issues. The device operators and OEMs lack in-house knowledge and skills related to OT provisioning workflows and key/certificate management specifications (e.g., Azure DPS, TCG/TPM, IoTSAFE/SIM, X.509 CSRs) required for IT-OT convergence, and the integration workflows for PKI and IoT cloud services-based device provisioning and lifecycle management.
-
OT/IoT/IIoT Devices
The high volume of heterogeneous devices in the Internet of Things (IoT), Industrial IoT (IIoT), and Operational Technology (OT) environments, in the order of billions, makes private key protection, key renewal/rotation, and key/certificate lifecycle management in Public Key Infrastructure (PKI) based environments extremely cumbersome and expensive for network operations center (NOC) and security operations center (SOC) operators in converged IT-OT environments. Performing certificate chain verification and processing certificate revocation lists are computationally and bandwidth intensive for applications on resource constrained devices. Local asymmetric keypair generation and periodic renewals for enhanced cybersecurity requires high entropy and compute capacity.
-
Symmetric Keys
The existing symmetric key generation and distribution methods manage pre-shared keys (PSKs) without adequately addressing the intricate workflows associated with the usage of the PSKs by applications executing on headless (non-user) devices and communicating with other devices in activities that include application data transfers, command and control messages, and telemetric data transfers. Further, the expiration and renewal of PSKs in use require timely synchronization between tightly coupled applications to avoid service disruption in production environments.
The fundamental gap in the adoption of symmetric pre-shared keys to implement cost-effective zero-trust networking is orchestrating the high velocity rotation and on-demand distribution of quantum-safe pre-shared symmetric keys to the client applications and services with simple APIs. A secure and scalable key distribution service requires domain-based groups for permissioned device memberships and authentication based on device domain validation and identifiers. -
Symmera DIN Solution
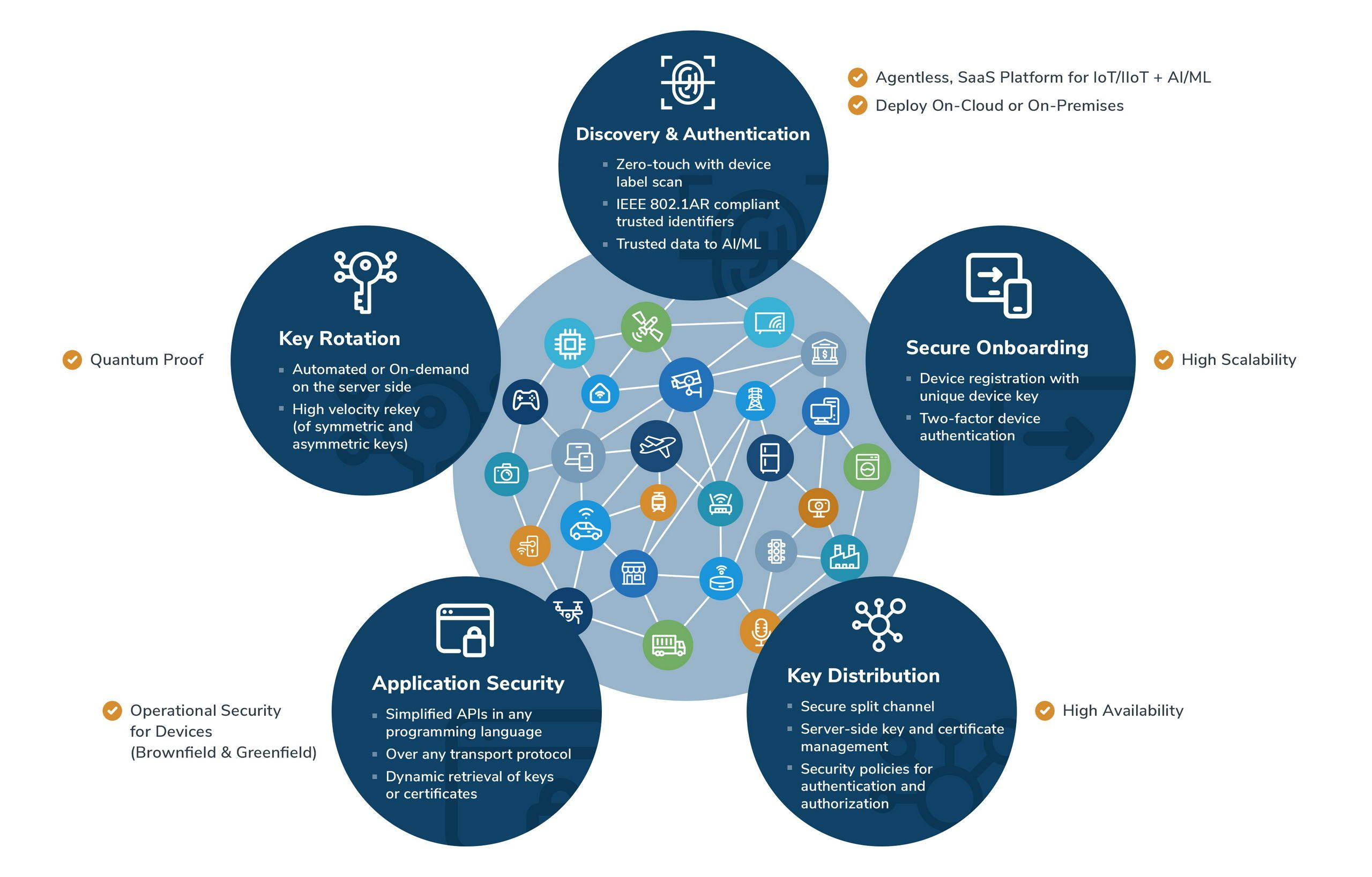
Symmera’s Distributed Intelligent Network (DIN) services provide trusted and verifiable device identity on the first mile with simple and cost-effective client authentication, data authentication, and data encryption for holistic protection from device to cloud. DIN solves the major device conundrum OEMs and end users face – devices need trusted identity and applications need protected session keys to transact with services (on-premises and in the cloud). In the race to a difficult IT-OT convergence solution, quantum-safe symmetric keys and key exchange methods are cost-effective and operationally efficient to implement simple, secure, highly available, and scalable solutions for cyber physical systems across industry segments – retail, industrial control systems, energy, manufacturing, logistics, transportation, healthcare, and defense.
Scalability, Availability, and Security
We enable secure field communications and trusted data streams from devices to microservices.
-
Simplified device provisioning workflow at factory, and application security by design to mitigate post-quantum crypto threats, avoid truck rolls for field service, prevent recalls
-
Device credentialing and discovery at scale with device label scan
-
Unified device onboarding and management workflow for IT/OT convergence, integrated with trusted network services (DHCP, DNS)
-
Mutual authentication and data protection with dynamic on-demand retrieval of symmetric keys or certificates, for resource constrained and resource slack devices, at lower TCO and increased operational efficiencies
-
High availability with automatic key rotations, certificate renewals, failover configuration, and secure export/import for persistence of the retrieved keys/certificates
-
Quantum resistant (and NIST approved) secure key exchange protocols and ciphers
-
Zero-touch key and certificate lifecycle management for two-factor device authentication, data integrity, and data confidentiality
-
Simplified device registration and trusted data streams to cloud hosted applications and services to connect, monitor, shadow, and control OT devices